BI.ZONE Mail Security
BI.ZONE Mail Security helps organizations of all sizes to mitigate the risk of cyberattacks, protect employees without impeding their productivity, and customize email security strategies
Defends people rather than inboxes: BI.ZONE Mail Security analyzes employee digital behavior and reveals hidden threats targeting corporate users
Contains complex AI‑based attacks, combats spam, phishing, spoofing, and malware attacks, and prevents the exploitation of mail server vulnerabilities
Ensures mail routing control across offices and branches
Balances peak traffic without decelerating user operations and losing correspondence
Featuring ML models for content‑based email classification, rating management, and detection of calls to action
Mail traffic management: hundreds of filter combinations and actions based on them
Proprietary multitenant technology
Interaction with third-party SIEM
Quick hassle-free cloud deployment
How it works
Personal account
Try it out
-
We will arrange a demo meeting and answer your questions
-
We will help you throughout the 30‑day trial period
You might also need
Publications
|
New BI.ZONE CESP protects against quishing, takes into account employee cyber awareness levels
April 26, 2024
|
Read | |
|
BI.ZONE CESP enables customized protection of corporate email
August 7, 2023
|
Read | |
|
BI.ZONE CESP swiftly responds to protect Outlook users against CVE‑2023‑23397
April 6, 2023
|
Read | |
|
BI.ZONE CESP reinforced to improve email protection
October 24, 2022
|
Read |
With significantly increased performance and enhanced intelligent filtering capabilities, BI.ZONE Mail Security now offers extra speed, convenience, and precision for both administrators and corporate users.
- 3x higher performance. The solution now processes up to 5,100 emails per minute on a minimum system configuration (8 CPU / 16 GB RAM).
- New Integrations section. Allows users to manage interactions with other security systems. Two built-in integrations are currently available, with four more expected by the end of the year.
- Proxy server support. Provides new capabilities for tasks requiring internet access in restricted infrastructures, such as working with BI.ZONE Threat Intelligence data or analyzing links in emails.
- Automatic deletion of old emails. Added along with soft rejection of incoming emails during CPU/RAM overload.
- AI model. Identifies calls to action in emails and learns from “Spam” / “Not spam” interface tags.
- Filtering for corporate data leak detection. Detects or blocks emails with attachments from being forwarded to external addresses.
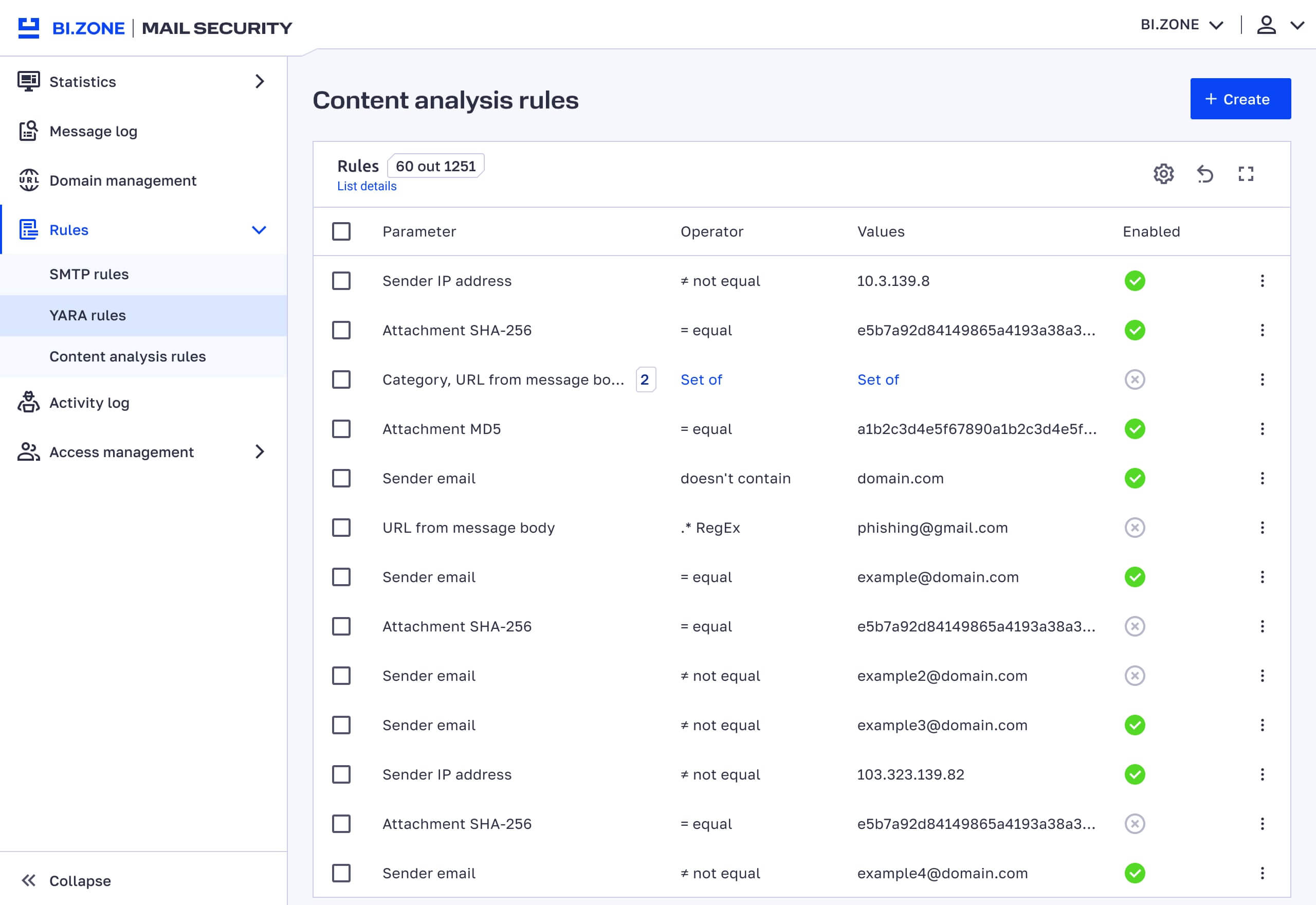
- Quick filtering rules. Block or allow messages by email address, domain, IP, subnet, or hash. Administrators can add these parameters individually or as lists (up to 10,000 entries).
- Advanced email traffic routing. Content analysis‑based management.
- Revised graylisting. Meets modern email protection standards.
- Enhanced content verification rules. The solution now accounts for DKIM, SPF, and file type.
- Auto-reply loop protection. Improves mail server stability and reduces load.
- Bounce message prevention. Restricts unnecessary delivery failure auto-replies.
- CLI installer. Speeds up on-prem installation and updates.
- Maximum flexibility. Up to 90% of system parameters can be managed via the interface.
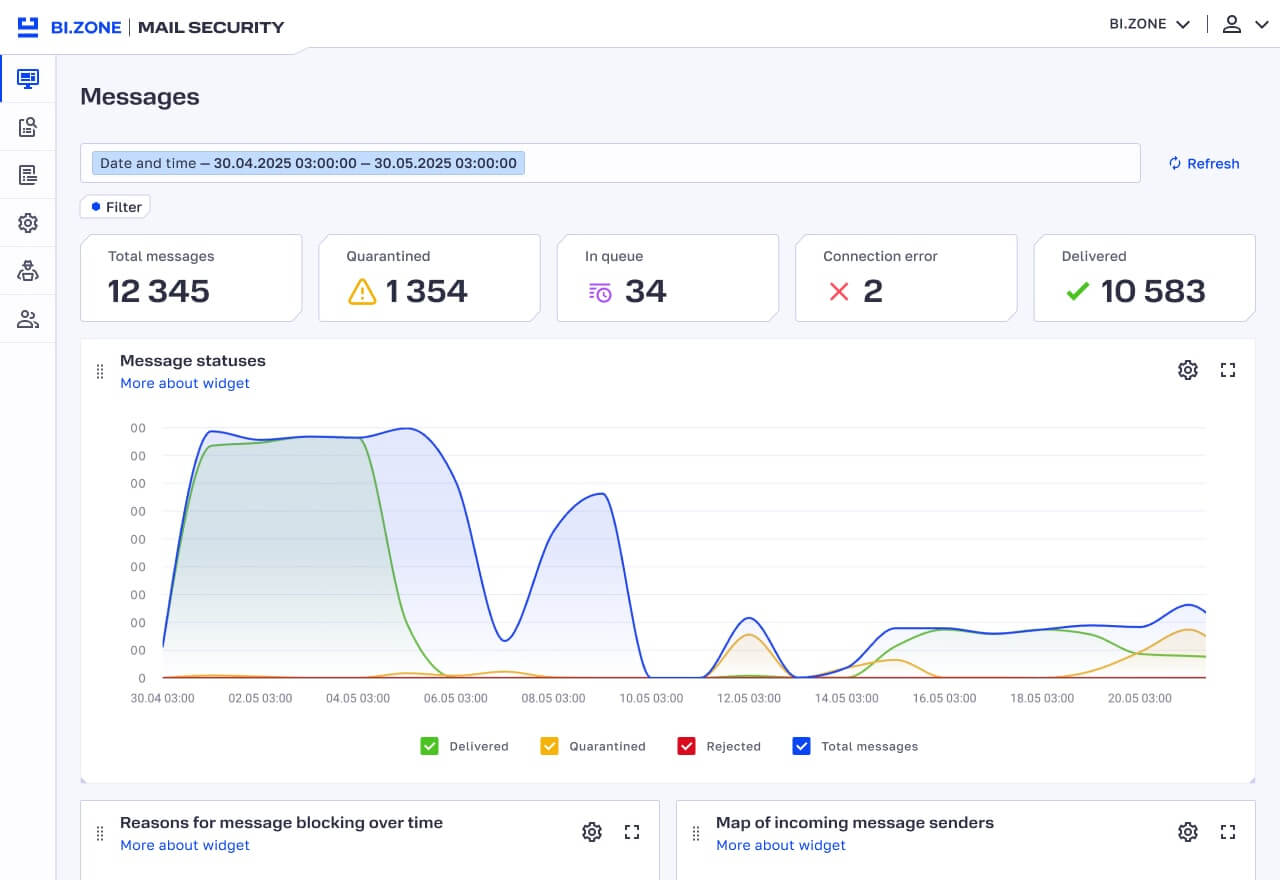
- Revised dashboards and key elements. Easier access to statistics and clearer data visualization.
- Enhanced action log and node monitoring.
- Updated handling of punycode and Cyrillic domains.
BI.ZONE CESP has been rebranded to BI.ZONE Mail Security. The product’s new version utilizes a high-performance kernel developed by BI.ZONE. From now on, the solution will evolve leveraging latest threat intelligence data.
- One more deployment option. Now the solution can be deployed on-prem.
- Much faster email checking and handling. With flexible filter settings, the system administrator can determine which emails must undergo detailed checks.
- Ability to balance the traffic and create a fault-tolerant cluster. This enables the processing of large volumes of email traffic.
- Multitenancy. In the on-prem version, this feature makes it possible to independently run multiple clients or branches in one application.
- Flexible backup management; flexible management of quarantine retention periods for various message categories; operations via API. This prevents the loss of information in emergencies.
- Email sanitization. Messages are delivered free of malicious content.
- Integration with third-party secure email gateways and sandboxes. This can provide an additional layer of protection.
- Editable email templates. This applies to quarantine notifications or undelivered messages for employees.
- Enabling and disabling the inspection of outgoing messages. The feature is available in the user’s personal account.
- Export of all actions with messages. The data is uploaded in the syslog format to external systems. Previously, only email incidents were transferred to SIEM systems.
The product’s new version provides additional protection for more vulnerable employees, detects malicious links in QR codes, and offers more clarity for email verdicts in the personal account space.
- Additional protection for more vulnerable employees. It has become possible thanks to greater integration with BI.ZONE Security Fitness, a platform for raising employee cyber awareness. By training with BI.ZONE Security Fitness, each user generates an individual rating reflecting vulnerability to social engineering attacks. This data now informs the email filtering process.
- QR code analysis. Thanks to machine vision, it is now possible to recognize a QR code in the email body and attachments. If the code contains a URL, the solution will analyze it along with other URLs to filter out phishing messages.
- Extended URL parsing. We constantly expand the range of readable characters and formats. Now we can detect malicious URLs behind HTML anchors, query parameters, and the ideographic full stop character 。.
- Improved statistical model. Even if attackers try to hide the number of recipients, the solution will detect a mass mailing. Such emails get a higher spam rating and are quarantined.
- CSV reporting. Now the administrator can email the output for any filter of the message log as a CSV document.
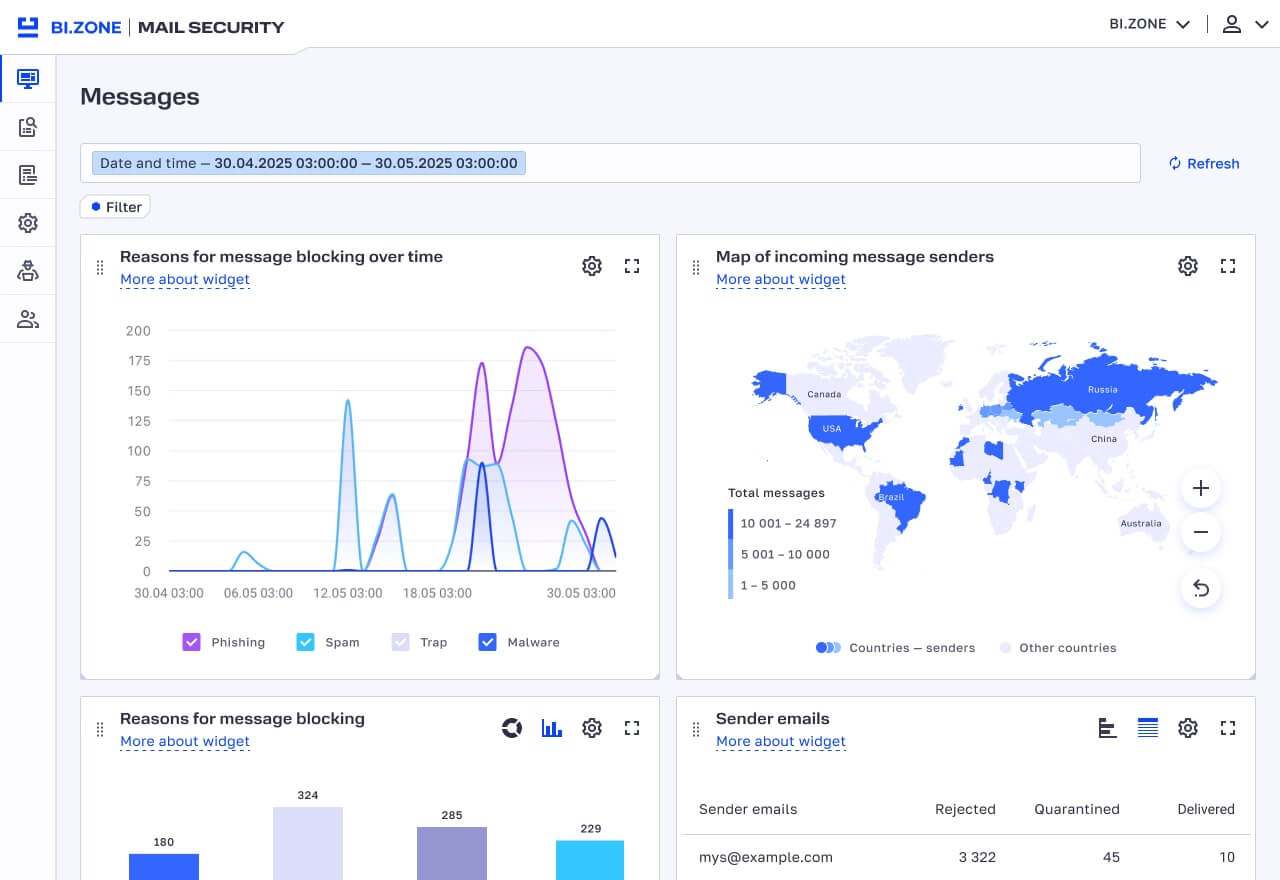
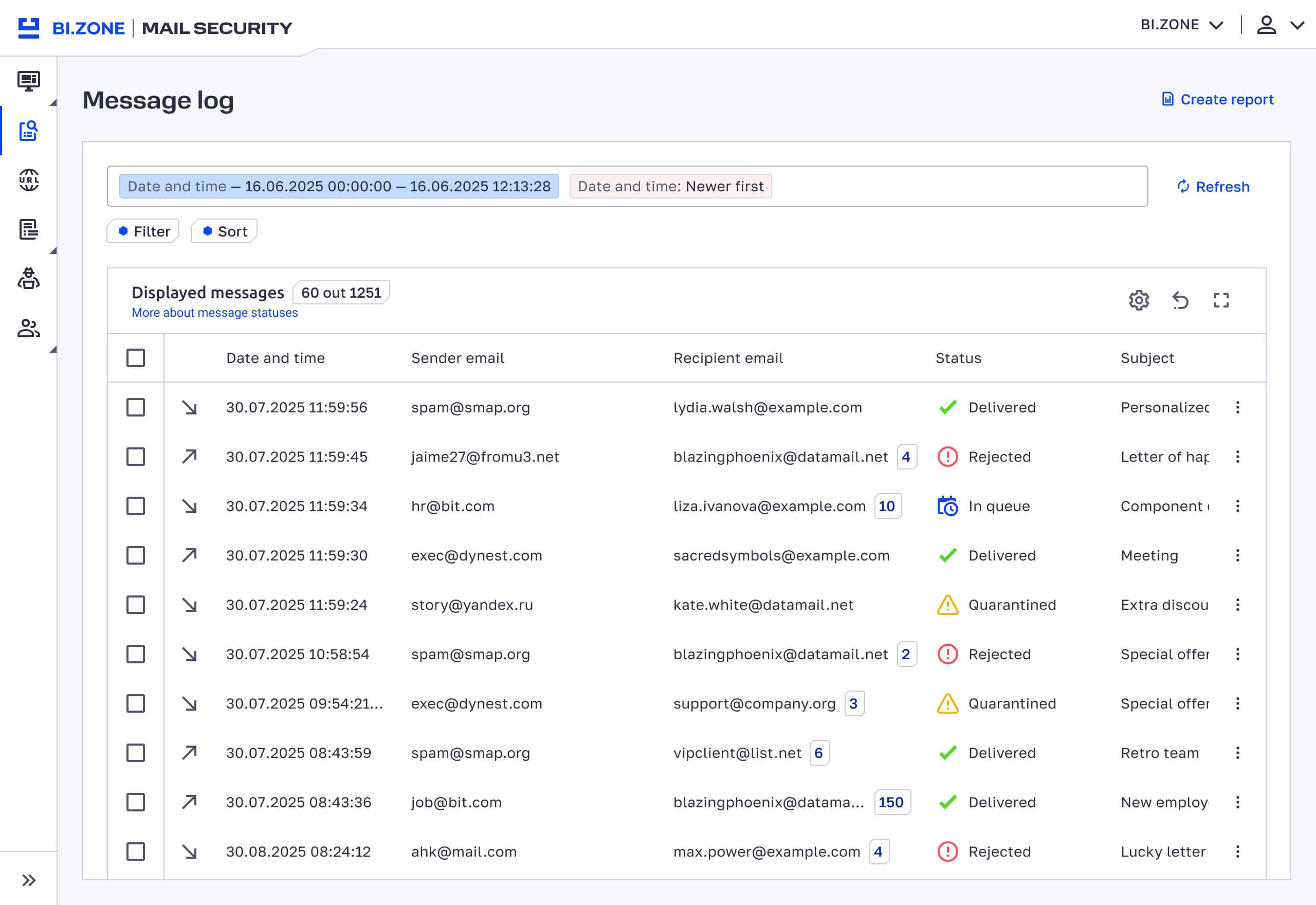
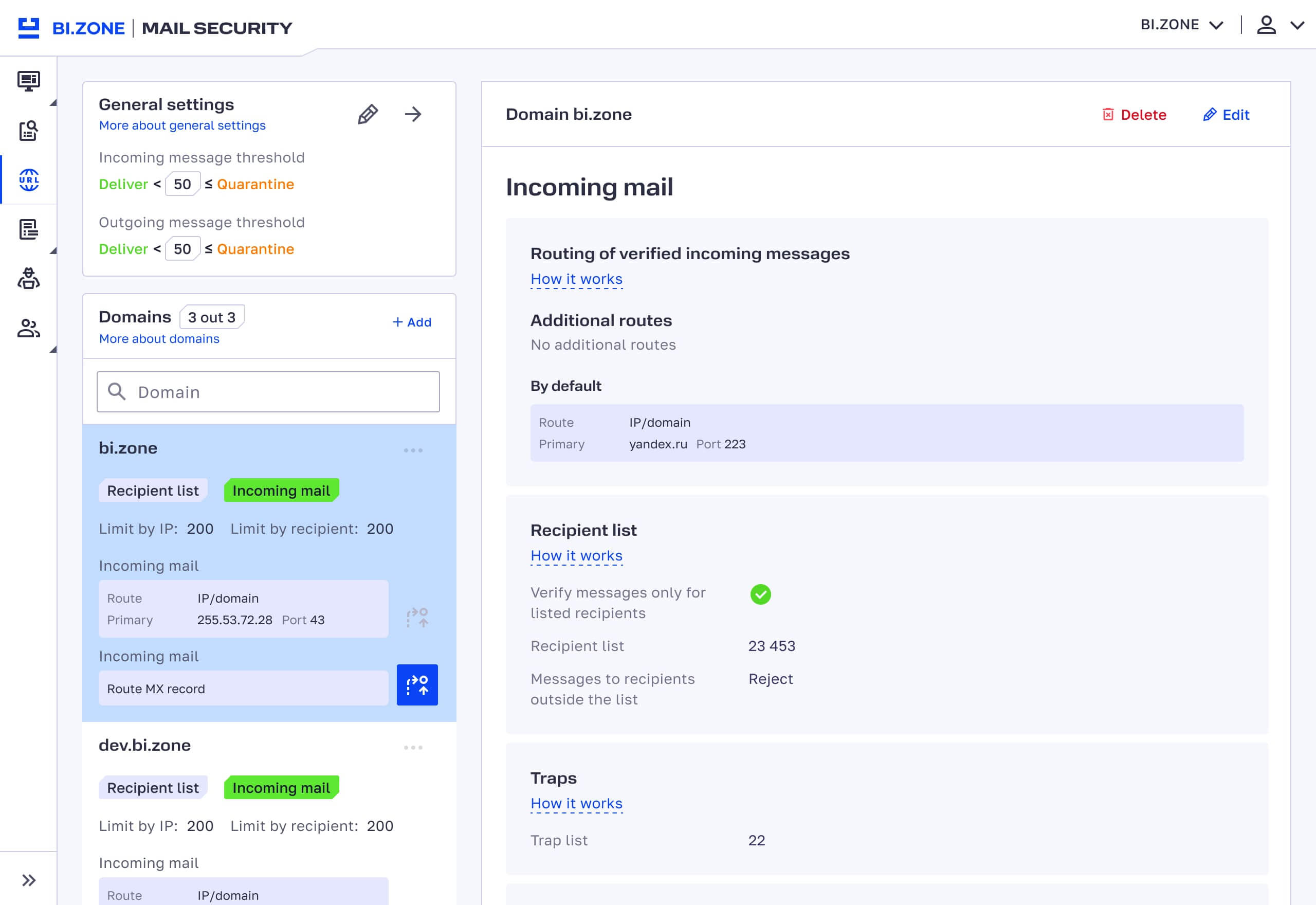
- More user-friendly message log. It is clear whether a message has been whitelisted, blacklisted, or assigned to extended filtering. If a message has links, the log will reflect web categories of the corresponding domains. There is also advanced filtering by delivery status, URL category, protected domain, and mail server response during delivery (250 OK, 500 Error, etc.).
- Security configuration statuses for domains. The updated solution offers more visibility into the security configuration process. With the process on the BI.ZONE side, you can see which of the four stages it is going through: synchronization, SMTP server verification, test email sending, or pending change of MX records.
Now it is easier to customize email protection, prevent data breaches, and analyze data in the personal account space.
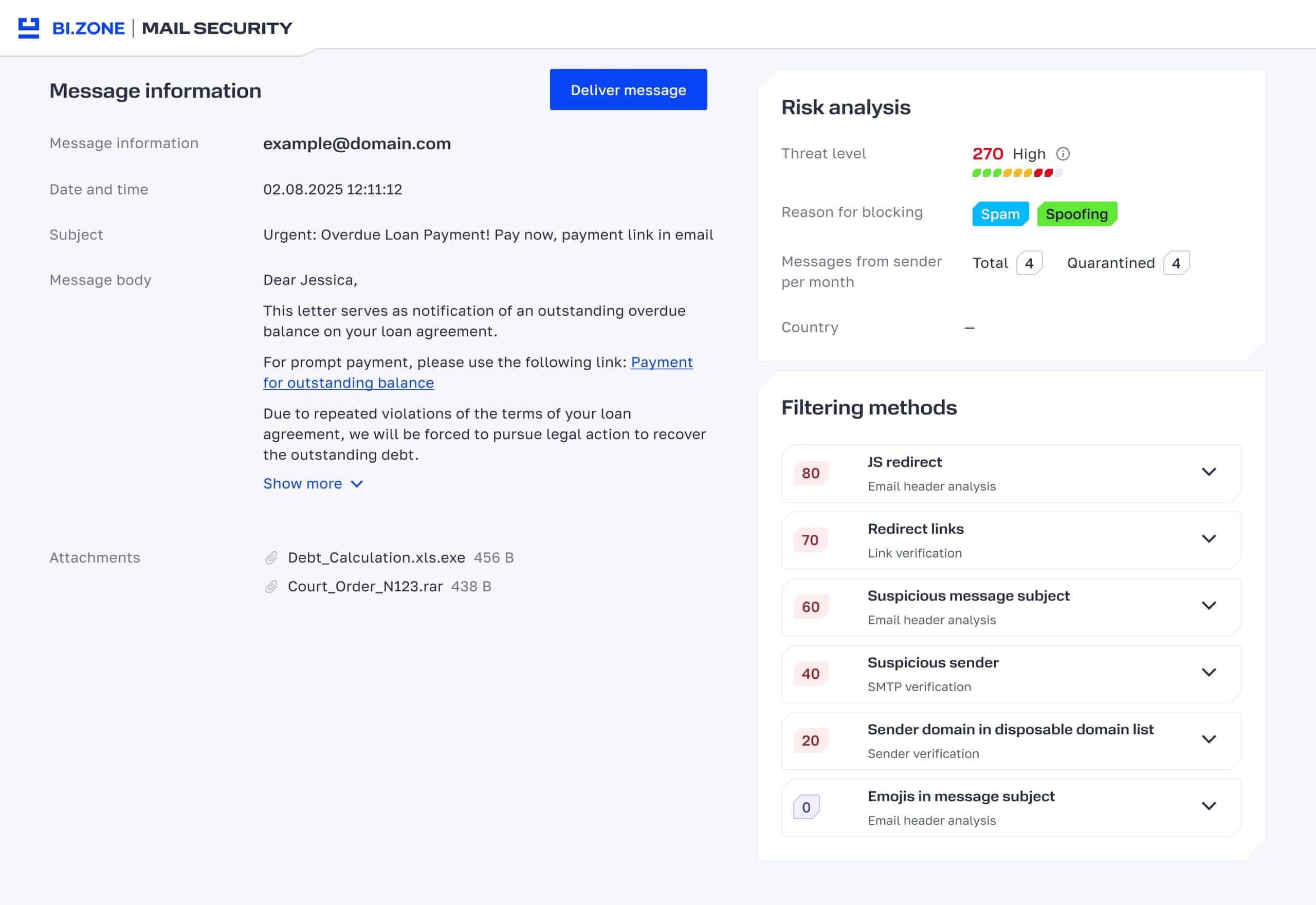
- Extended filtering. Now users can configure over 20 parameters that will influence the spam rating of their correspondence. For instance, incoming messages with links to public file sharing websites or outgoing messages with attached scans containing company seals can be considered more suspicious.
- Integration with BI.ZONE Security Fitness. Employees can in one click notify security teams of suspicious messages—directly from the email client interface. The new opportunity has become available thanks to the integration with BI.ZONE Security Fitness, a solution for preventing social engineering attacks.
- Additional guarantee for email delivery. The capability for monitoring public reputation lists (databases used for filtering out illegitimate traffic) has been expanded and automated. Companies whose IP addresses are mistakenly included in such lists will not experience any correspondence delivery issues as we will timely contact the reputation list owners and fix the problem.
- Enhanced machine learning model. It analyzes the body of the incoming email, the subject line, links in the text, and service headers. This makes it possible to more accurately determine whether a message is legitimate or potentially dangerous.
- User profiling. Now each user has a unique profile based on the number of emails the user sends and receives daily. This enables the detection of anomalous activity that may indicate an attack or an account compromise.
- Extended protection from spoofing. The service can now recognize Unicode spoofing and automatically identify typos, incorrect domain extensions, etc. in seemingly legitimate sender domains.
- Improved algorithms. We have significantly improved three mechanisms: the automated search for malicious code in HTML documents; the automated search for phishing links; and the password enumeration algorithm for secure archives.
- Service cost linked to the number of accounts. The interface now has a window with the number of email accounts included in the service cost. If you want to check whether extra addresses affect the cost, you can download the full list of emails in CSV format.
- Email processing results. View detailed information to see what mechanisms influenced an email’s rating. This will help you create rules for the extended filtering list.
- Senders map. Now you can see the email flow on a map in your personal account. You will be able to learn from which country emails come most often.
The filtering system is now more efficient: we have improved the protection mechanisms and added new ones.
- Behavioral analysis. Previously, only the recipient could influence the sender’s reputation by releasing the message from the quarantine. With the update in place, the system also takes into account the actions of the solution’s administrator.
- Detection of illegitimate outgoing correspondence. The system is now better at filtering outgoing messages. This improves the reputation of the mail server IP addresses and increases the chances of emails to reach their destinations.
- File analysis. The service can now analyze password‑protected files. It will try to guess the password for an attached archive to scan it for malware.
- Detection of phishing links. The search capability has been extended to detect and analyze links within files and archives.
Email is the most popular attack vector, so protecting it is an essential aspect of any security strategy. The number of attacks is growing with each year, which means that the risk of breaching sensitive data is also increasing. That is why choosing effective defense systems is so important for a company’s security.
You need to set complex passwords for email accounts and use encryption algorithms. Both can be implemented in different ways, such as using programs, plug-ins, or applications that automatically create keys and encrypt transmitted data. However, this may not be enough. Adversaries go far beyond hacking email accounts or intercepting correspondence. They often use social engineering techniques to trick the victim into sharing the information they need. Therefore, it is better to make sure that dangerous messages do not reach their targets. Specialized services address this security issue. They filter traffic so that nothing suspicious gets into your inbox.
1. Spam
This threat includes any unsolicited messages with questionable or promotional content. Spam does not involve fraud and does not contain malware attachments that can encrypt data or steal passwords. Nevertheless, spam can be very intrusive and distracting, making it difficult to find the information you need.
2. Flooding
Email flooding is the sending of an overwhelming number of emails to a target address or domain. These emails are often meaningless and may contain random sets of words or characters. The sheer purpose of email flooding is to overload the recipient’s inbox and make it unusable.
3. Malware
A malware program may look like a regular attachment but is in fact dangerous. Such programs help attackers access the victim’s computer remotely, compromise personal data, and disrupt business operations. Malware attachments are masked in many different ways: a malicious file may have a PDF icon or a seemingly harmless extension (.pif, .vba, .cmd, .ps1, .doc, .xls, .jar, .pdf, .zip), etc.
4. Spoofing
This involves cybercriminals faking emails from legitimate senders. Adversaries impersonate a credible source to gain the user’s trust and access their information.
5. Server compromise
This attack implies the use of exploits. These are special programs (code fragments or command sequences) that enable adversaries to exploit vulnerabilities in the endpoint software. The goal is to gain control of the system and perform various illegitimate actions (i.e., steal data or change user rights and privileges).
6. Business email compromise, BEC
BEC is a form of phishing attack where a criminal uses email to gain the victim’s trust and persuade them to perform illegitimate actions.
Different threats require different approaches.
Spam, flooding. Configure security settings of your mail server and in the domain zone / DNS server: DKIM, DMARC, ARC, SPF, PTR, RBL, whitelisting/blacklisting/graylisting.
BEC, spoofing. Develop software add‑ons for sender profiling and email behavior analysis. To better detect spoofing, you also need add‑ons for signature analysis.
Malware. Install antivirus software on endpoints.
Server compromise. Configure the firewall’s security policy for incoming network packets and regularly update server/user software.
No matter what threat you encounter, we recommend using a dedicated email security solution. Raising cyber awareness of your employees and training them is also important.
Special attention should be paid to such forms of phishing as BEC and spoofing. The success of such attacks depends on the actions of employees; that is, on the human factor which causes 95% of cybersecurity issues
Phishing refers to a group of cyberattacks where adversaries employ social engineering techniques to present scam messages as legitimate ones to win the recipient’s trust. This group includes BEC, spoofing, vishing, and other types of cyber threats. The overall goal is to trick the victim into performing actions that will result in a sensitive data breach, such as the revealing of corporate passwords or payment card details.
Initially, phishing implied emails with malicious attachments or links to fraudulent websites. Over time, the term has evolved to include other methods and their combinations:
- fraudulent text messages (SMS phishing or smishing)
- posts in instant messengers and social networks
- fake websites and internet advertising
- phone calls (voice phishing or vishing)
In the course of a cyberattack, adversaries manipulate people, appeal to their emotions, and abuse their trust. Here are examples of scenarios based on the exploitation of emotions:
- Fear. An incoming message says that the data on the user’s computer will be destroyed. All it takes to prevent the deletion is to click a link.
- Negligence. Recipients fail to notice a typo in the sender’s domain:
gmail.con,yadnex.ru. - Greed. The attached coupon offers a 55% discount applicable only in the next 15 minutes.
- Frustration. Users are forced to click a link to unsubscribe from annoying newsletters.
- Willingness to help. An employee receives a message, “Your colleague made a mistake in the report. He must fix it ASAP. Do you happen to know his phone number?”
- Credibility, urgency. A purported tax authority demands an immediate payment of a fine.
Although numerous in variety, all phishing attacks involve deceiving people for financial or other gains. Let us take a closer look at several types of phishing.
Spearphishing
Targeted phishing attacks focus on a specific person or organization to make them reveal sensitive information. To reach their goals, adversaries may create personalized content. This requires more time and effort than a standard phishing attack, as criminals have to collect the necessary information first to create a sense of familiarity with their victims. Such information may include names and job titles of specific employees, their email addresses, etc.
For example, an employee responsible for payment authorization may receive a seemingly legitimate message from the company CEO with instructions to pay a large sum of money to a supplier. The message may contain a link to a fake payment system from which the funds will be transferred to the scammers’ account.
419 fraud, or the Nigerian letter scam
This type of scam first emerged in Nigeria in the pre‑internet 1980s. A typical victim would receive a letter from a foreign sender asking for assistance in getting a large sum of money. For whatever reason, the sender is unable to receive the money on their own, therefore is asking for help in exchange for a hefty fee. In this scheme, the criminals get hold of the victim’s funds in one of the two ways:
- ask the victim to provide their banking account details and promise to credit funds to this account if the victim first pays a surcharge
- convince the victim to grant access to their banking account
One of the most well‑known examples is a message sent on behalf of a Nigerian prince or another high‑ranking person asking for urgent assistance in getting several million dollars out of Nigeria.
Such phishing attacks are also known as “419 fraud,” with the number referring to an article of the Nigerian criminal code.
Phone phishing
Includes vishing (voice phishing) and smishing (sms phishing), which employ fraudulent phone calls and text messages, respectively.
Adversaries may additionally use phone phishing and boost the effectiveness of targeted attacks by combining emails with calls and SMS.
A typical example of vishing: a scammer introduces himself as a police officer, a tax official, or a bank security officer and starts intimidating the victim. For instance, they say that the victim’s banking account has been blocked or suspended due to a court ruling that needs to be appealed right away. After that, the scammer tries to persuade the victim to reveal passport and banking details or provides the account number to which the victim should pay the fine.
When it comes to phishing, the size of an organization and its resilience to cyber threats are of little importance. Phishers achieve their goals through social engineering rather than trying to find a breach in the perimeter. A company can implement a variety of defense measures—security tools, VPN, two‑factor authentication—and still fall victim to phishing. Strong passwords and antivirus programs are not enough—it is important to take care of security at all levels.
An example of how devastating a phishing attack can be is the 2019 case of the Norwegian aluminum giant Norsk Hydro. It all started with a company employee unknowingly opening an infected email with a ransomware attachment. The message was sent from a real Norsk Hydro customer and signed with a trusted certificate. Several months later the criminals unleashed a full‑scale attack, which, according to the company’s earnings report, cost Norsk Hydro an estimated 70 million dollars in losses
Such situations prove that organizations need to consider risks, use all opportunities to strengthen security, and resist phishing both inside and outside the perimeter.
The service can protect your inbox from a range of threats.
1. Bot activity
Scammers can use bots for different purposes. One scenario is the exhaustion of a mail server’s resources so that the server stops receiving messages.
BI.ZONE Mail Security checks the correctness of an SMTP dialog using regular expressions and supports graylisting to filter out emails sent by bots.
2. Spamming and flooding
Employees receive unwanted content that floods their inboxes and hinders business communications.
BI.ZONE Mail Security recognizes spam mailings by analyzing the subject and body of emails based on public reputation lists and its own linguistic self-learning model. As a result, the service filters unwanted messages before they even reach the mail server.
3. Malicious attachments
A single launch of a malicious program may affect an entire IT infrastructure: the malware can spread throughout the corporate network, encrypt data, compromise accounts, etc.
BI.ZONE Mail Security prevents such programs from reaching your device by using several antivirus engines and the BI.ZONE Threat Intelligence portal.
4. Server compromise
It allows mail server vulnerabilities to be exploited for illegitimate activities, such as remotely executing commands to steal data or change a user’s access level.
Our experts keep up with news about vulnerabilities in mail server software. If exploiting a vulnerability requires the manipulation of email traffic, our team quickly creates security rules. This will help you maintain security until a software upgrade.
5. Embedding of phishing links
Clicking such a link often results in compromised credentials.
BI.ZONE Mail Security blocks emails with phishing links. To achieve this, the service does the following:
- generates a statistical model of the sender’s reputation
- examines the HTML markup of the email for hidden text, images, URL and CSS links
- recognizes QR codes
- uses FQDN/URL/IPv4 indicators from the BI.ZONE Threat Intelligence database
6. Spoofing
Adversaries may fake a credible source and take advantage of the user’s trust: obtain passwords to authorize in the corporate network, change security settings, and access sensitive information.
BI.ZONE Mail Security can detect if the sender is spoofed by applying a number of email authentication methods, such as SPF, DKIM, DMARC, and others. The service also recognizes Unicode spoofing, and typosquatting, when attackers deliberately misspell legitimate web addresses.
7. Business email compromise (BEC)
In BEC attacks, scammers do not just mimic someone else’s email account, they hack it and use it to send messages. For example, a request to transfer a payment to a new account may come from the email address of a trusted contractor.
BI.ZONE Mail Security prevents BEC attacks with a combination of checks. It targets different types of threats and includes, for example, ML‑based linguistic analysis, as well as statistical and behavioral models, such as individual profiling.
The service also uses these mechanisms to check outgoing email messages for phishing or spam. This helps to identify a compromised account and prevent malicious mailings from being sent on behalf of the protected company.
8. Data leaks
Through emails, trade secrets or personal data can fall into the wrong hands. This is not always due to malicious intent. It can also be a matter of ignorance toward security policies.
BI.ZONE Mail Security allows you to set up individual rules for checking outgoing mail to avoid leaks. For example, thanks to the use of machine vision technologies, you can enable searching for blue company seals in email attachments.
BI.ZONE Mail Security is already integrated with the BI.ZONE Threat Intelligence portal to receive the latest cyber threat data. The portal aggregates information about potential security threats from both internal and external sources (BI.ZONE and its partners). BI.ZONE Mail Security leverages this intelligence to assign each message a spam rating, an indicator of how likely a particular message is spam.
The BI.ZONE Threat Intelligence portal collects information about artifacts that have been seen in malicious activity. BI.ZONE‑CERT (computer emergency response team) manages and validates this data. Thus, artifacts discovered by BI.ZONE-CERT during its research work enrich the threat database shared with BI.ZONE Mail Security. When an email with similar artifacts comes to the server, this message will be quarantined immediately.
Yes, BI.ZONE Mail Security works with servers that use encryption for email traffic. You should always use an encrypted connection, otherwise outsiders can intercept your traffic and gain access to confidential information.
An SSL/TLS connection is established between the sender’s mail server and the BI.ZONE Mail Security filtering nodes. Only then your email is transferred: the filtering nodes analyze it and securely deliver it to your server.
Yes, if your mail server supports the STARTTLS technology. The BI.ZONE Mail Security filtering nodes must use an encrypted connection to deliver filtered and legitimate email. This makes it possible to protect messages from interception. Adversaries can only recognize the type of encryption or the approximate amount of data, but will not be able to see the content.
No, we do not support this technology. We filter traffic between mail servers and do not install any software on user devices. Therefore, we cannot check messages protected by S/MIME, a standard for public key encryption and signing.
Yes, BI.ZONE Mail Security supports this feature: it allows you to establish connections between mail servers which have to use encryption.