BI.ZONE CPT
Continuous Penetration Testing
Recurring security assessment of the external IT perimeter
Solution overview
BI.ZONE CPT reduces vulnerability life cycle through in-depth assessment of your infrastructure. Unlike classical penetration testing, CPT checks are performed frequently while retaining the highest quality standards
30+
experienced CPT experts certified by CREST, Offensive Security and other leading international agencies
100%
of false positives filtered out by manual verification of each vulnerability
Monitoring
Track changes in your IT perimeter and the status of vulnerabilities on a daily basis
Optimization
Improve perimeter security management, save on procurement and configuration of scanners and manual verification systems
Scalability
Add company branches and web/mobile applications for centralized vulnerability management
Compliance
Generate reports for regulators at any convenient time
How it works
Our experts monitor your external IT perimeter for any changes and perform comprehensive vulnerability checks in your infrastructure. We manually verify the detected vulnerabilities and provide remedial recommendations.
The data is aggregated on a single portal, BI.ZONE CPT. Through this portal, you can track changes in your perimeter, stay up-to-date on detected vulnerabilities and their remediation status and consult with BI.ZONE experts. This information can be uploaded to your monitoring system via the API
Data safety is our priority
- BI.ZONE CPT undergoes regular in-house security checks
- We apply SDL principles to BI.ZONE CPT
- BI.ZONE CPT is designed with the defense-in-depth approach
Project stages
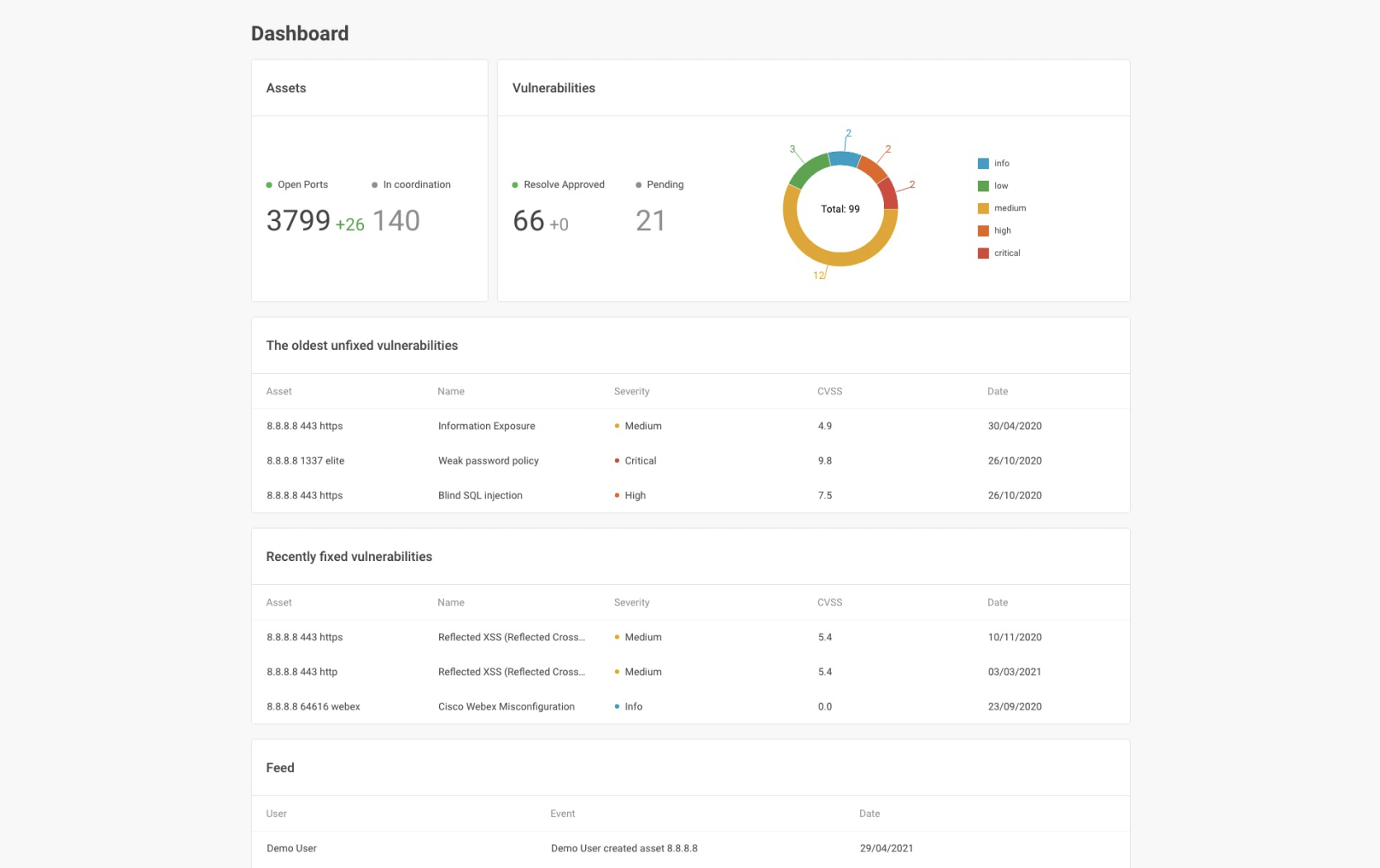
Dashboard
Product certifications
BI.ZONE services are certified to ISO 9001 and ISO 27001
Our team
BI.ZONE expertise is recognized by leading global organizations
Ask our experts
You might also need
Package options
| Service | Basic
Frequency
|
Advanced
Frequency
|
|---|---|---|
|
Scanning the external IT perimeter and web applications
|
Every two weeks
|
Weekly
|
|
Monitoring and expert evaluation of changes in the services
|
Monthly
|
Weekly
|
|
Searching for new network nodes on the external IT perimeter
|
Monthly
|
Twice a month
|
Additional services
BI.ZONE Red Teaming
Imitation of a hacker attack. Develop the skills of your cybersecurity team
BI.ZONE Security Fitness
Simulated phishing emails. Improve cyber awareness among your employees